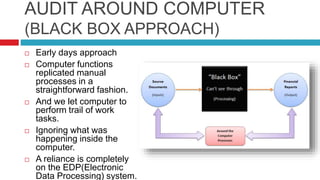
Accounting Information Systems, 5 th edition James A. Hall COPYRIGHT © 2007 Thomson South-Western, a part of The Thomson Corporation. Thomson, the Star. - ppt download
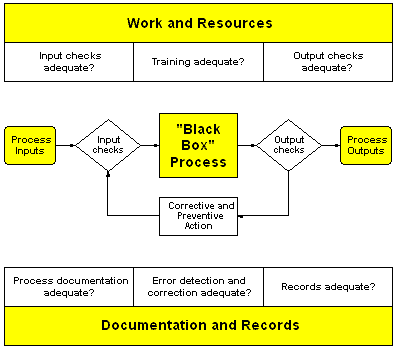
![PDF] Distill-and-Compare: Auditing Black-Box Models Using Transparent Model Distillation | Semantic Scholar PDF] Distill-and-Compare: Auditing Black-Box Models Using Transparent Model Distillation | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/752fd6f73c0840e5919180441c3c575da4a41124/2-Figure1-1.png)
PDF] Distill-and-Compare: Auditing Black-Box Models Using Transparent Model Distillation | Semantic Scholar

PDF) A Distributed `Black Box' Audit Trail Design Specification for Connected and Automated Vehicle Data and Software Assurance

1 Output Controls Ensure that system output is not lost, misdirected, or corrupted and that privacy is not violated. Exposures of this sort can cause serious. - ppt download